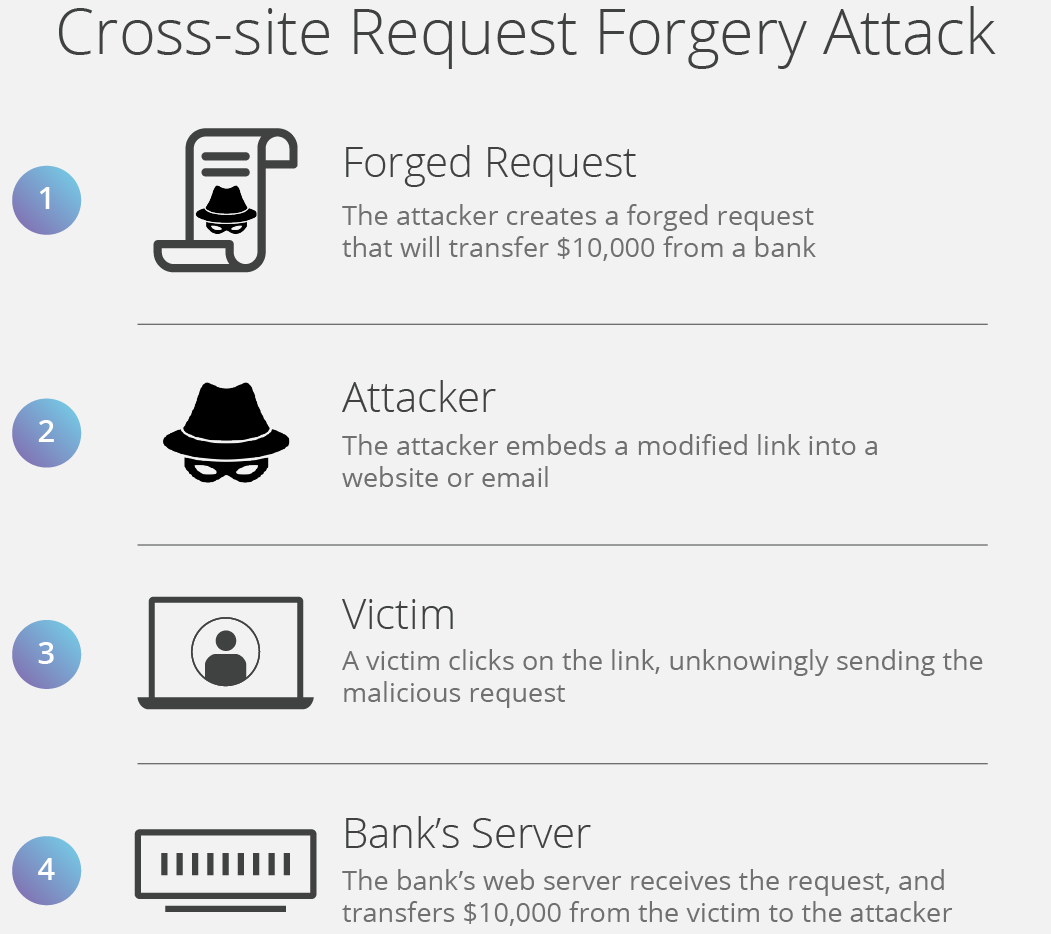
Fine Beautiful Info About How To Prevent Csrf
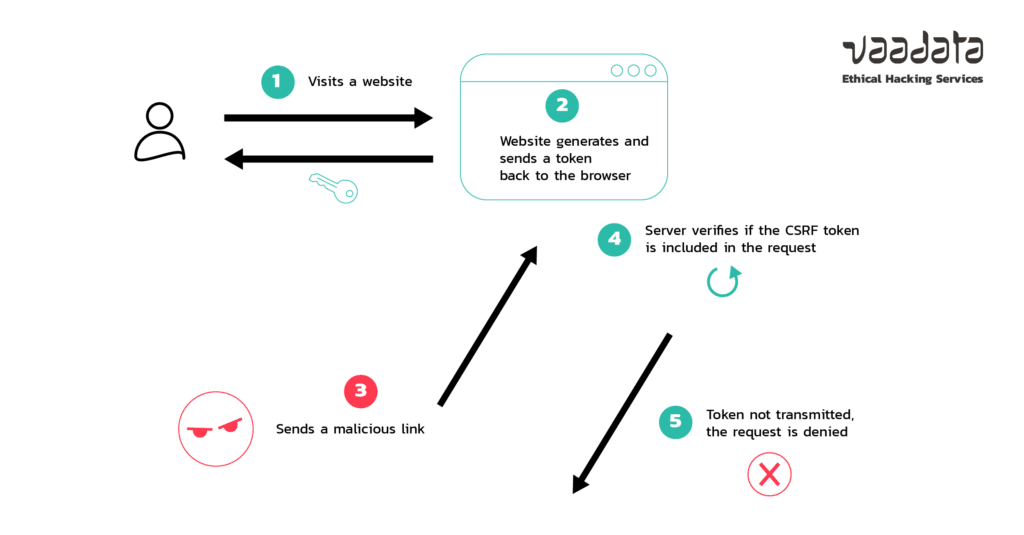
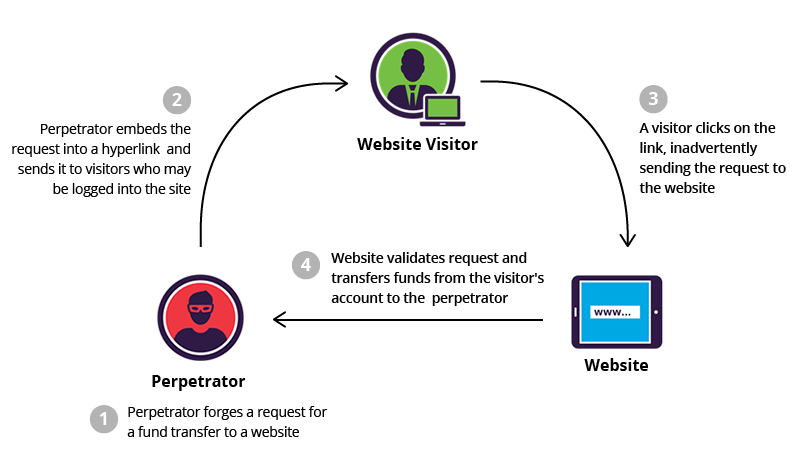
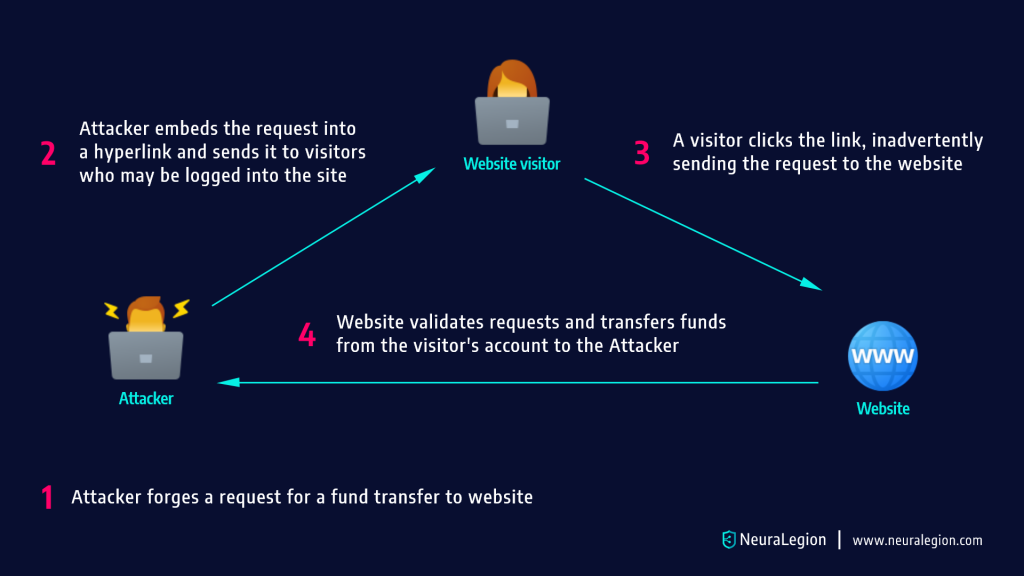
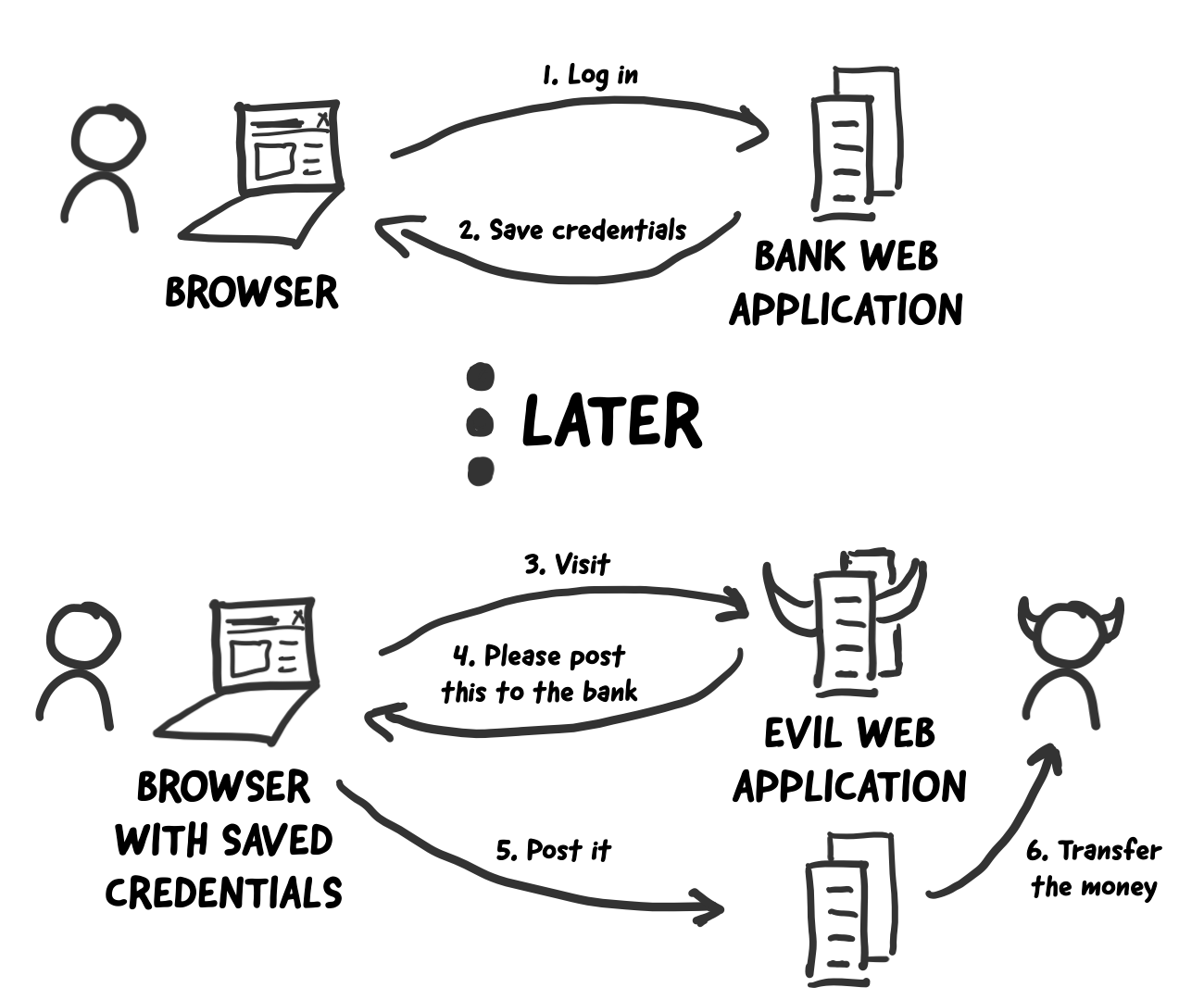
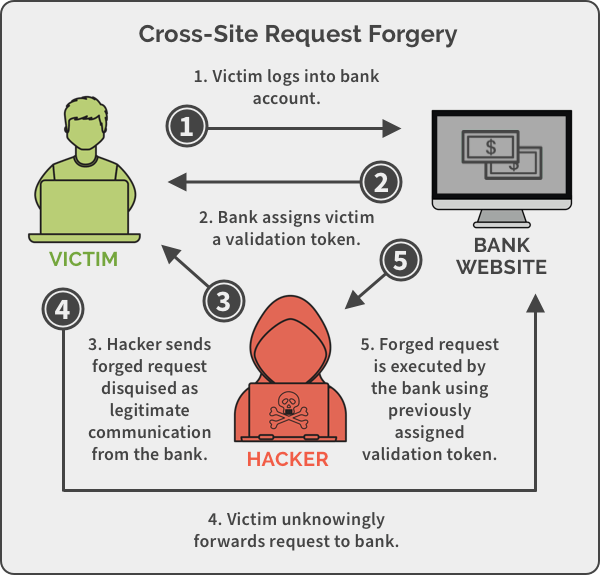
Csrf tokens prevent csrf because without token, attacker cannot create a valid requests to the backend server.
How to prevent csrf. The csrf token can be. The basic way to prevent csrf is to implement csrf tokens, while avoiding the weaknesses we described in the previous section. You can adhere to the following best practices to prevent csrf attacks:
Fortunately, csrf attacks can be prevented. Unpredictable with high entropy, as. Below is a list of.
If you use something like window.location most likely you should not expect referal data to be present. Here are additional ways you can prevent. For.net, add a session identifier to viewstate with mac (described in detail in the dotnet security cheat sheet ).
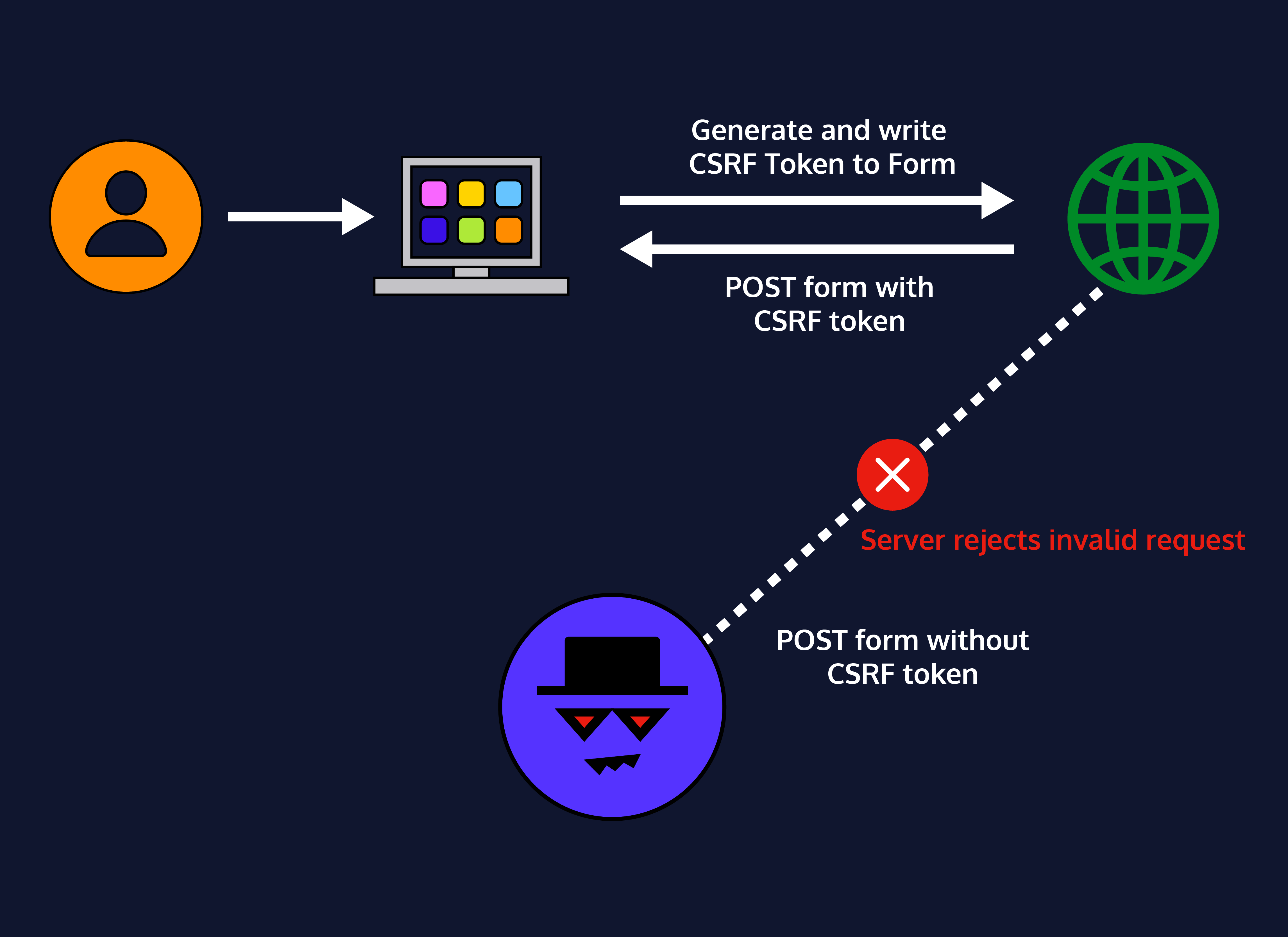
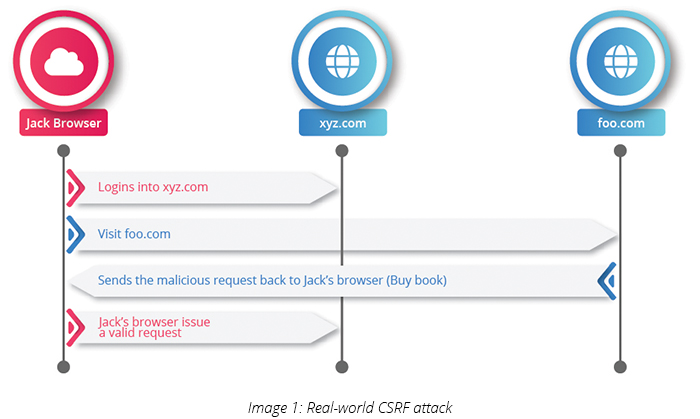
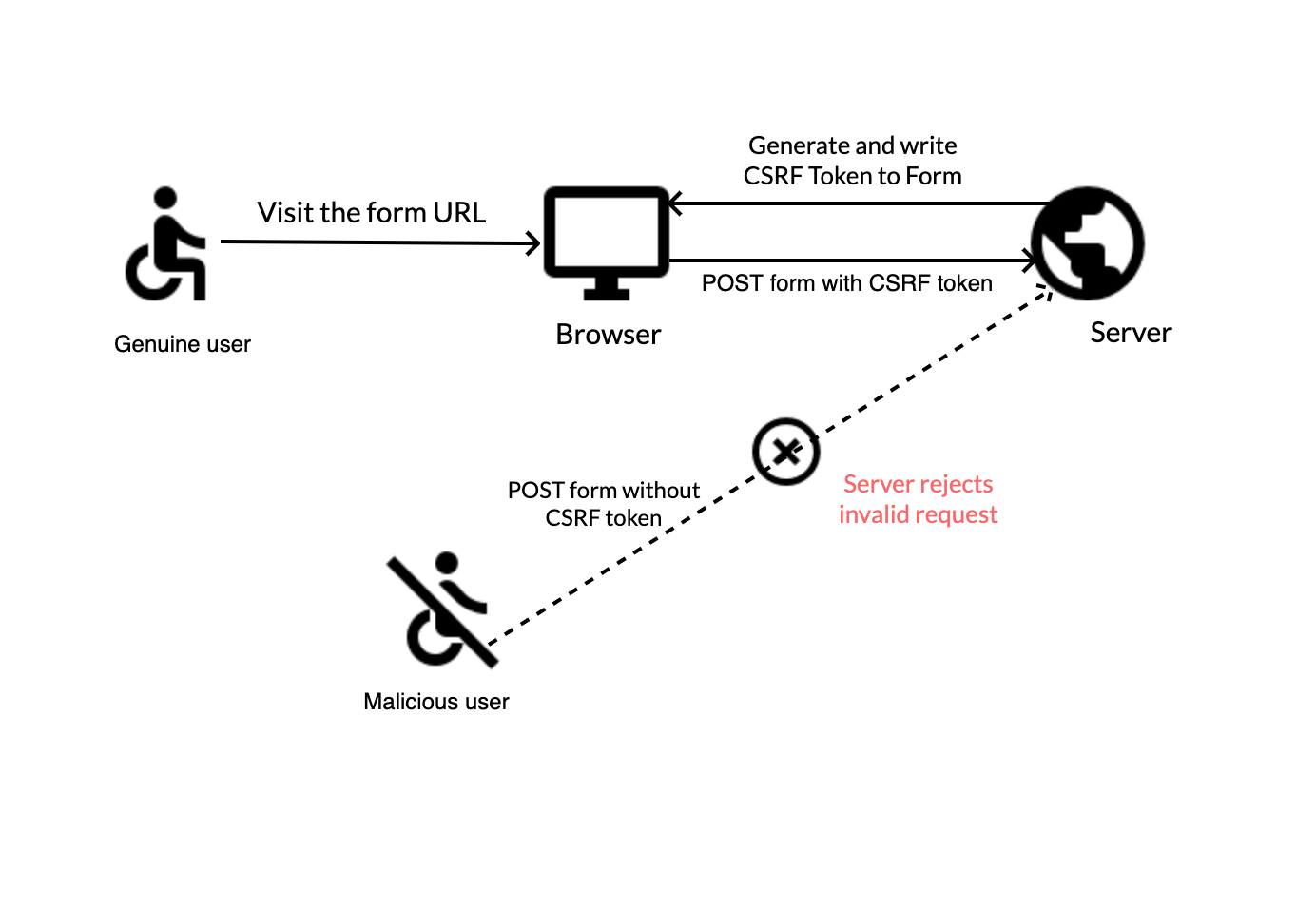
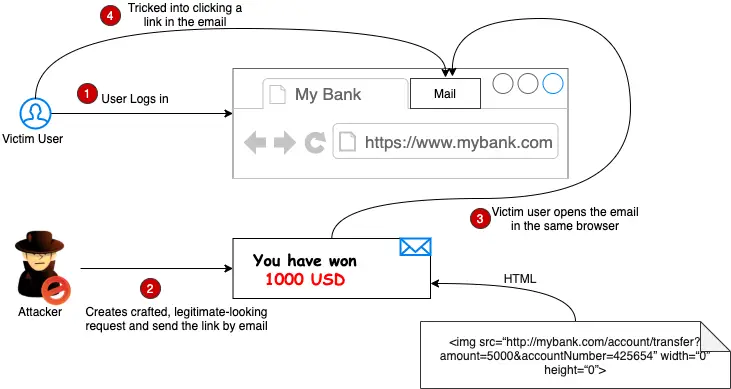
A popular method for csrf prevention is to not use cookies and always pass state. This article discusses the stored csrf attack and explores some examples and prevention strategies to prevent the stored csrf vulnerability. Preventing csrf attacks the most robust way to defend against csrf attacks is to include a csrf token within relevant requests.
Now we dive into the topic of how to best prevent a csrf attack. Let’s look at some of the most efficient ways to safeguard your website. How to stop csrf attacks choose your frameworks carefully.